I am showing an alternative approach to embedding your payload. In this method, the focus will be on stealth as we override a legitimate function

Cyber Security Architect | Red/Blue Teaming | Exploit/Malware Analysis
by Rio Asmara Suryadi

I am showing an alternative approach to embedding your payload. In this method, the focus will be on stealth as we override a legitimate function

Hi Fellow reverser Playing around with the code reversing, I am sharing a small review on the topic related to obfuscation Code obfuscation is like

I would like to share a basic tutorial on reverse engineering related to Windows API calls. This tutorial will involve reviewing a substantial amount of

This is yet another technique for injecting payloads into memory. We recognize that the majority of the techniques used involve similar steps. Nowadays, EDR is

As the incident responder, evaluating a security breach can be a stimulating task. It requires the ability to connect various pieces of information in order
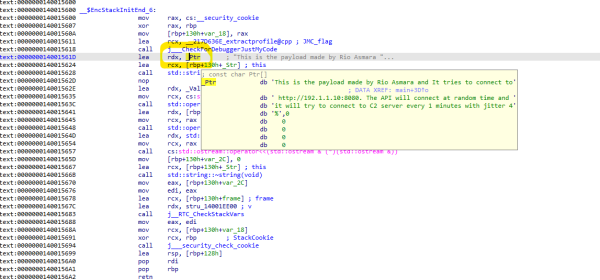
My Friends, Just a quick simple and very basic tutorial on how to create an automation to extract malware configuration from PE file. I made