Just to continue from my previous post, I conducted an exercise involving the exploitation of a host specifically designed to contain two vulnerabilities: CVE-2023-38146 and CVE-2023-28252.
I will be presenting my exercise from the perspective of forensic analysis. To enhance the effectiveness of the analysis workflow, I am utilizing CyberTriage to analyze and correlate various data.
I have gathered evidence from the compromised host using CyberTriage’s offline collection feature. Upon loading the results into the application, it took less than 10 minutes to identify the critical artifacts. These artifacts were utilized for exploiting vulnerabilities and navigating the victim machine with CobaltStrike.
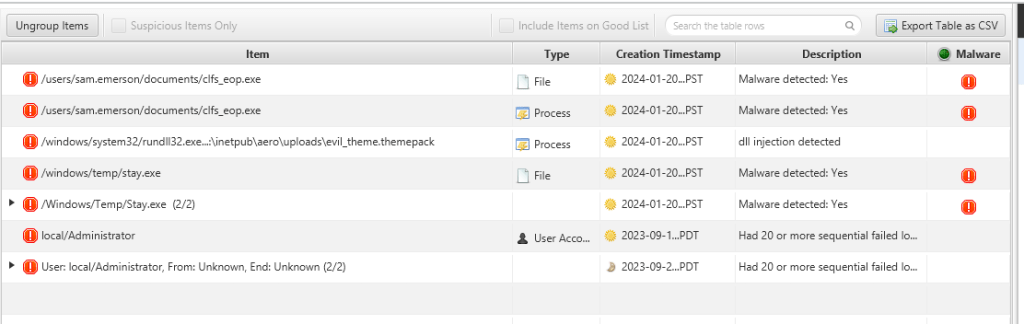
Account Analysis
It has been confirmed that a persistent mechanism has been implanted, which will be triggered every time a new user session is initiated on the victim’s machine. It is evident that a beacon is activated when logging in as the administrator.

Look at the correlated events from the account of administrator we can see that a malicious process has been identified
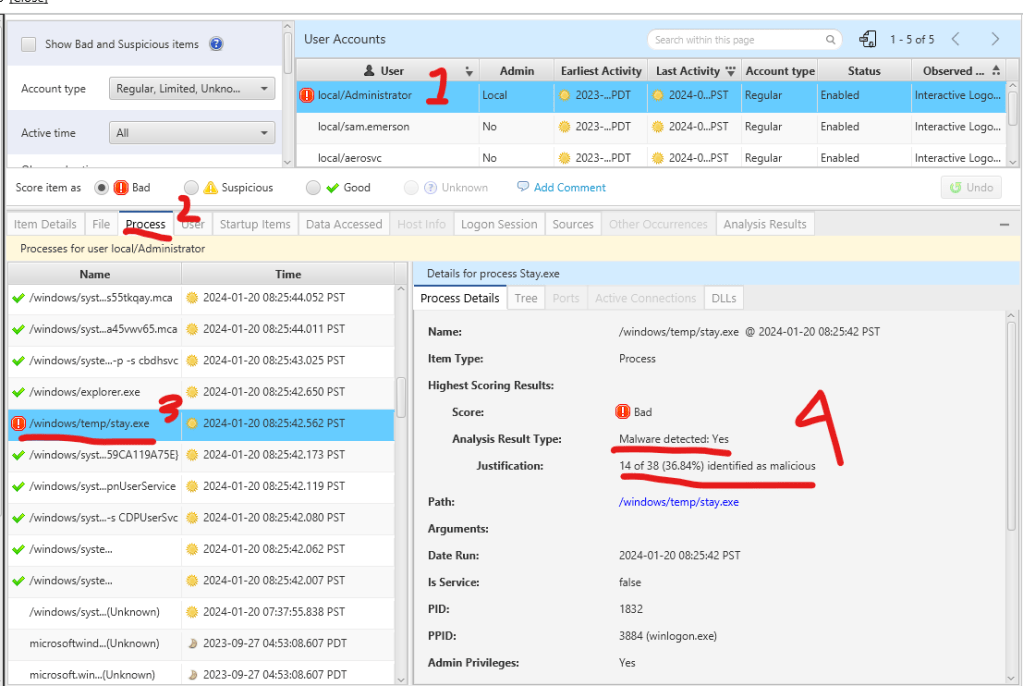
We can observe from the relationship between the parent and child processes that stay.exe is initiated at the beginning of the operating system startup, as the parent of stay.exe is winlogon.exe. It is uncommon for an unknown executable to become a child of winlogon.exe, unless it is malicious, such as persistent malware.

Lets look to another account that could have been compromised as well which is sam.emerson
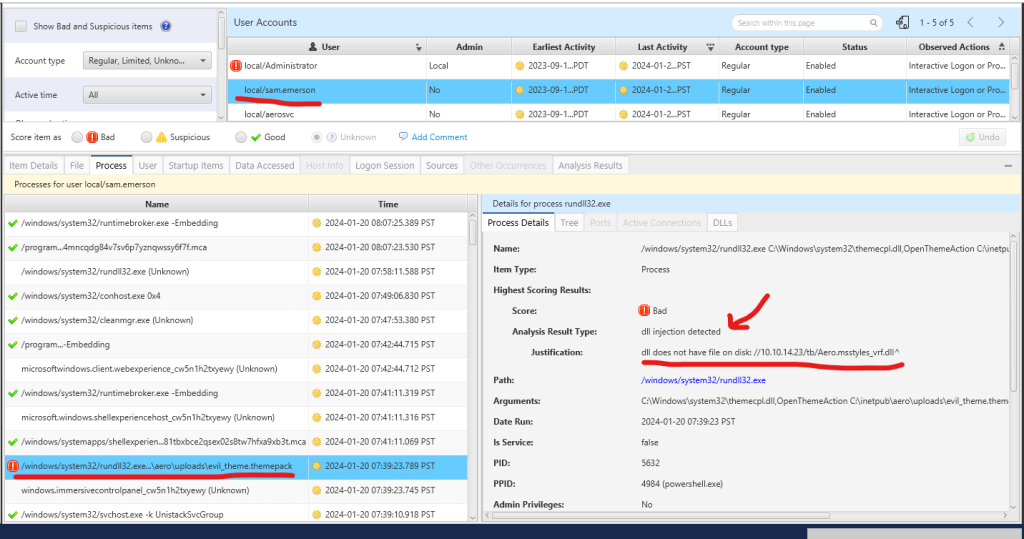
We have identified a process flagged as malicious due to its detection of conducting DLL injection. As mentioned in my prior post, this is the file utilized to establish the initial foothold, exploiting CVE-2023-38146 through themepack exploitation.
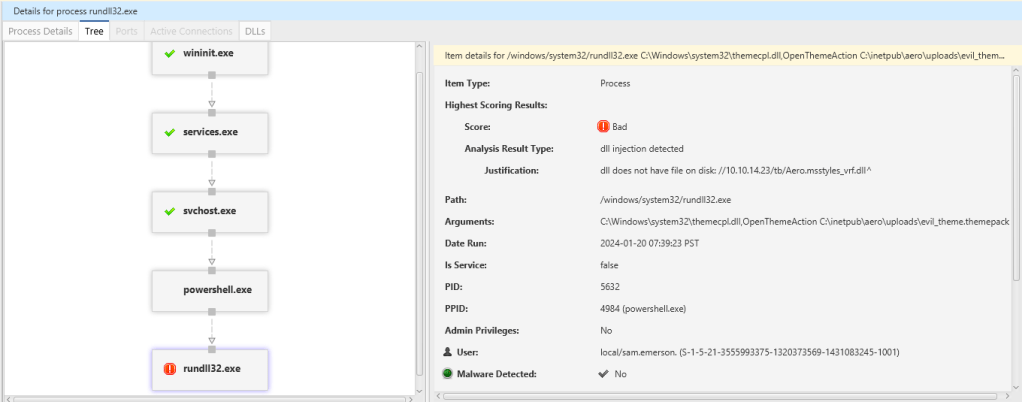
“Upon examining the process tree, it is evident that there is another concerning behavior: the use of rundll32.exe as a child process of PowerShell. The analysis indicates that rundll32.exe is being utilized to load a DLL located on the attacker’s machine with the IP address 10.10.14.23 (which corresponds to my Kali Linux machine).”
As we have identified that the user sam.emerson has been compromised, it is advisable to flag this account as suspicious. This action will aid in future analyses as CyberTriage can correlate the events triggered by sam.emerson.
Running Process Tree Analysis
We have discovered an additional application, cifs_eop.exe, running from the same directory as the previously discussed process. As mentioned in my previous post, I utilized this executable to exploit the CVE-2023-28252, which resulted in a beacon connection. CyberTriage has flagged this as malicious due to being detected by 10 out of 38 scan engines.

Another piece of useful information for identifying malware is the time interval between its creation and execution. Typically, malware is delivered to the victim and then executed shortly thereafter, resulting in a relatively short time gap between these two events.

You can observe that conhost.exe has a child process called clfs_eop.exe, as I executed clfs_eop.exe from the beacon originating from conhost.exe.

Active Network Connection Analysis
We can clearly observe that the processes are establishing connections with another machine at 10.10.14.23. This allows us to establish a correlation between the IP address 10.10.14.23 and the previous finding, where the exploit dll was hosted. Consequently, we can determine which processes have been compromised. It is important to note that, in order to conduct a more thorough analysis of the malicious payload, we can extract it from the processes listed below from the memory acquisition

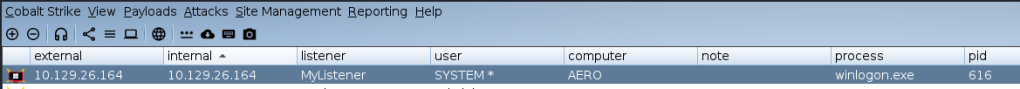
On the analysis below, it can be inferred that the machine has been completely compromised, as the process making outbound connections is under the NT AUTHORITY/SYSTEM. This indicates that the adversaries have active full privileges on the victim machine.

This is from the CobaltStrike point of view
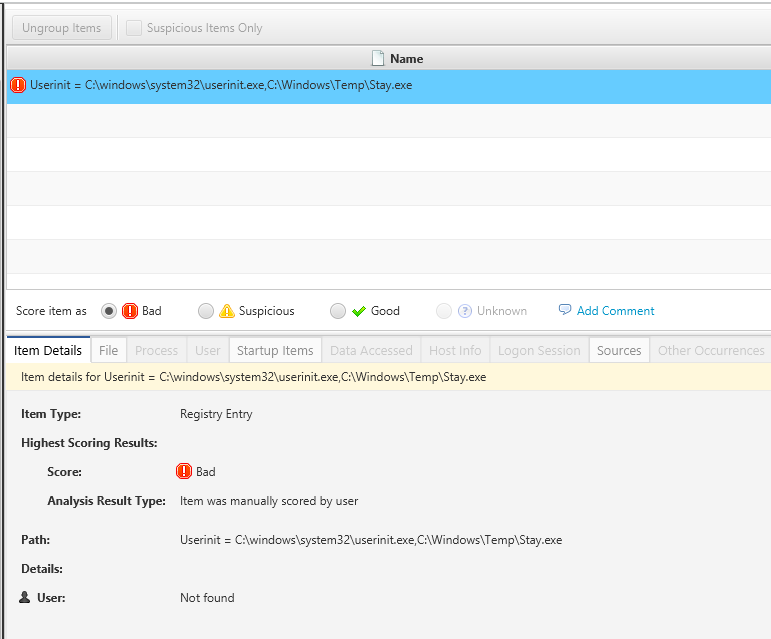
Registry Item Analysis
CyberTriage has successfully retrieved a crucial artifact pertaining to the method of malware persistence. As mentioned in the preceding post, I established persistence using staykit to ensure that the malware runs each time the user session is initiated.