Hi Everyone
Today I am going to continue the jorney of penetration test for Bilubox. At this point, I am going to explain the step of finding the exploitable bug based on the information we got fro the previous steps.
lets start from phpmyadmin application. We know that the version of phpmyadmin is 3.4.7.
The first thing to get exploit information is using searchploit here is the steps
- open the console in the kali linux
- type searchploit phpmyadmin and there will alot of collection of exploit regarding phpmyadmin. We can see there is one exploit that related to the phpmyadmin with version the same with ours.
output of searchploit phpmyadmin

one of exploit available for our phpmyadmin version
![]()
You can check the exploit detail description by typing searchploit -x exploits/php/webapps/18371.rb
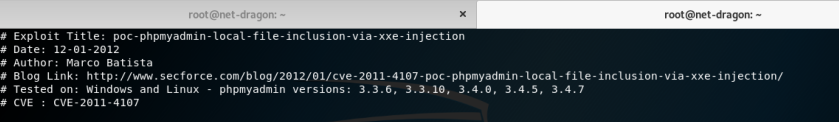
after the above information we can see that the exploit successfully tested not at our version which is 3.4.2
We can try to gather exploit information from metasploit, it is very easy to be used and powerfull framework.
launch your metasploit framework and do the following
type search phpmyadmin

we can see from the above information that there are some exploit regarding phpmyadmin including the discolusure that give us when the exploit came out and it’s rank, the better the rank means the more possibilities the exploit will successfull. it is recommended to use the best “excellent” exploit for successfull attack.
You can go further down go to the detail of each exploit, for example you want to use exploit/multi/http/phpmyadmin_null_termination_exec then you can type like the below in the metasploit
use exploit/multi/http/phpmyadmin_null_termination_exec
show options
I will give the detail on how to use metasploit in the different post.
The one that you should not forget is to look the information on google regarding the vulnerability also check on gihub.
as we can see the detail, most of the exploit requires phpmyadmin authentication to do successfull attack. but in this phase we do not have it yet. To reduce the time taken, lets put aside phpmyadmin exploitation for a while an we go forward to another alternative
I will do the credential hunting in the other post. 🙂
One comment