Binary analysis and malware detection have long been the domain of highly specialized security researchers armed with deep assembly knowledge and endless patience. Traditional malware analysis required analysts to manually reverse engineer suspicious files, compare assembly code line by line, and spend hours identifying subtle differences that could indicate malicious behavior. But what if I told you that this painstaking process has been revolutionized by combining three powerful technologies: BinDiff, Binary Ninja, and AI integration via Model Context Protocol (MCP)?
The Traditional Challenge
Imagine you’re a security analyst who discovers a suspicious file in a user’s download folder—what appears to be rundll32.exe. Your first instinct is to compare it with the legitimate version from C:\Windows\System32\. In the past, this meant:
- Loading both binaries into a disassembler
- Manually comparing function by function
- Analyzing assembly code differences
- Identifying which changes might be malicious
- Documenting findings across multiple tools
This process could take hours or even days for complex binaries, and required deep expertise in assembly language and Windows internals.
Enter the Modern Trinity: BinDiff + Binary Ninja + AI
The integration of these three technologies has created an unprecedented analysis capability that transforms how we approach malware detection:
BinDiff + Binary Ninja: The Perfect Analysis Partnership
The power of modern binary analysis comes from combining BinDiff’s quantitative comparison engine with Binary Ninja’s advanced reverse engineering platform. BinDiff revolutionized binary comparison by automatically identifying identical, similar, and different functions between two binaries, storing detailed comparison metrics in SQLite databases including function matching confidence scores (0.0 to 1.0), basic block similarities, call graph analysis, and instruction-level change tracking.
Binary Ninja complements this perfectly by providing direct programmatic access to reverse-engineered code through its modern API. Where BinDiff tells you what changed with statistical confidence, Binary Ninja shows you how it changed by converting assembly to readable C-like pseudocode (HLIL), enabling multi-binary session management, and allowing real-time switching between suspicious and legitimate binaries to extract identical functions for side-by-side comparison.
Together, they create a comprehensive analysis workflow: BinDiff identifies functions worth investigating through quantitative metrics, while Binary Ninja provides the actual reverse-engineered code to understand the behavioral implications of those changes.

AI Integration via MCP: Intelligence-Driven Analysis Orchestration
The recent integration of AI via Model Context Protocol (MCP) has transformed binary analysis by enabling AI to intelligently select and coordinate between multiple MCP tools—choosing dynamically between BinDiff MCP connections for database queries and Binary Ninja MCP connections for code analysis based on investigation needs. This creates an unprecedented level of analysis orchestration:
- Intelligent MCP Tool Selection: AI autonomously chooses between BinDiff MCP and Binary Ninja MCP tools based on analysis objectives
- Dynamic Database Access: AI connects to BinDiff SQLite databases via MCP when statistical analysis is needed
- Adaptive Code Analysis: AI switches to Binary Ninja MCP connections when reverse-engineered code examination is required
- Cross-Platform Data Correlation: AI intelligently coordinates between MCP tools to correlate database metrics with actual code implementations
- Automated Tool Orchestration: AI builds comprehensive analysis workflows by selecting appropriate MCP connections for each investigation phase
The real magic happens when BinDiff’s rich SQLite metadata is combined with Binary Ninja’s powerful reverse engineering capabilities, with AI intelligently selecting the appropriate MCP tool for each analysis phase.
Real-World Example: Detecting a Sophisticated Rundll32 Trojan
Let me walk you through a recent analysis that demonstrates this powerful combination in action.
The Setup
- Suspicious File: downloaded_rundll32.exe
- Reference File: Legitimate rundll32.exe from Windows System32
- Tools Used: Binary Ninja with MCP AI integration
The Analysis Process
Step 1: AI Selects BinDiff MCP Tool for Database Analysis
AI intelligently chooses the BinDiff MCP tool to connect directly to SQLite databases when statistical comparison data is needed:
-- AI autonomously selects BinDiff MCP tool and queries SQLite database
SELECT
f1.name as func1_name,
f2.name as func2_name,
m.similarity,
m.confidence
FROM function_matches m
JOIN functions f1 ON m.func1_id = f1.id
JOIN functions f2 ON m.func2_id = f2.id
WHERE m.similarity < 0.9 -- Functions that changed
ORDER BY m.confidence DESC;
-- AI Result: DoesSecurityPolicyAllow shows 0.75 similarity (triggers Binary Ninja MCP selection)Step 2: AI Switches to Binary Ninja MCP Tool for Code Extraction
Based on BinDiff analysis results, AI autonomously selects the Binary Ninja MCP tool to access reverse engineering capabilities and extract identical functions for comparison. The AI strategically chooses tools based on investigation needs:
- Function implementations by choosing Binary Ninja MCP tool for reverse engineering access
- Assembly and HLIL code through intelligent MCP tool selection for code analysis
- Function metadata by switching between appropriate MCP tools based on data requirements
- Cross-references and call graphs via strategic Binary Ninja MCP tool utilization
The AI’s ability to intelligently select between MCP tools enables autonomous analysis orchestration, choosing the right tool for each investigation phase without manual intervention.
Step 3: AI Orchestrates MCP Tool Coordination for Cross-Correlation
The AI demonstrates sophisticated tool selection by leveraging BinDiff MCP insights to guide Binary Ninja MCP utilization. Based on the SQLite similarity score of 0.75 retrieved via BinDiff MCP, the AI intelligently chooses to:
- Switch to Binary Ninja MCP tool to extract DoesSecurityPolicyAllow from suspicious binary
- Maintain Binary Ninja MCP connection to extract the same function from legitimate binary
- Coordinate between MCP tools to compare function signatures, parameters, and implementation logic
- Synthesize analysis results by intelligently combining data from both MCP tool connections
The AI’s intelligent MCP tool selection allows autonomous decision-making about which analysis capabilities to employ based on quantitative database findings and investigation requirements.
Step 4: AI-Guided Code-Level Assessment with Binary Context
The AI analyzed code from both binaries simultaneously, providing contextual comparison:
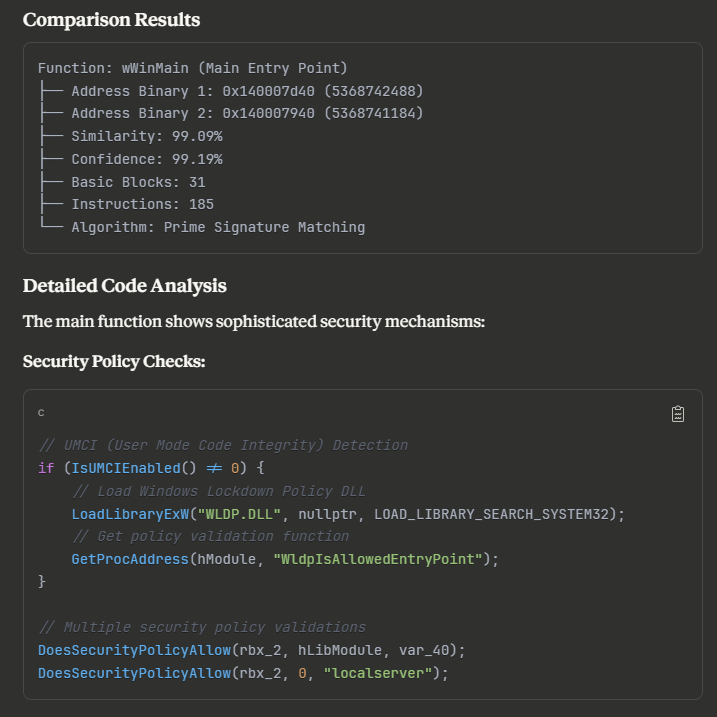
AI Analysis: “Direct code comparison reveals critical differences:
SUSPICIOUS Binary (downloaded_rundll32.exe):
NTSTATUS DoesSecurityPolicyAllow(int64_t policy_func, int64_t hModule, int64_t context) { NTSTATUS result = IsUMCIEnabled() if (result.b != 0) { if (policy_func != 0) result = policy_func(0, hModule, context, &output) // 3 params - suspicious result.b = output != 0 } else { result.b = 1 } return result }LEGITIMATE Binary (system32_rundll32.exe):
NTSTATUS DoesSecurityPolicyAllow(int64_t policy_func) { NTSTATUS result = IsUMCIEnabled() if (result.b != 0) { if (policy_func != 0) result = _guard_dispatch_icall(policy_func) // 1 param - standard result.b = result == STATUS_SUCCESS } else { result.b = 1 } return result }Critical Finding: The suspicious binary captures additional context parameters (hModule, context) that the legitimate version doesn’t collect. This indicates potential function output manipulation.”
Step 5: SQLite-Driven Evidence Collection
The AI generated a comprehensive analysis report including:
- Technical function differences
- Security implications
- Threat classification
- Recommended actions
The Results
What would have taken hours of manual analysis was completed in under 10 minutes with definitive results:
- Verdict: Downloaded rundll32 identified as malware masquerading as system binary
- Technique: Social engineering + sophisticated evasion
- Risk Level: High (system-level access trojan)
- Action: Immediate quarantine recommended
The Advantages of This Modern Approach
1. Real-Time Comparative Analysis
- Traditional: Load one binary, analyze, take notes, load second binary, analyze separately
- Binary Switching: Load both binaries once, switch seamlessly during analysis, compare live code side-by-side
2. Contextual Function Analysis
- Traditional: Analyze functions in isolation from each binary
- Binary Switching: Analyze same function across both binaries with full context preservation
3. Immediate Code Verification
- Traditional: Rely on BinDiff visual comparisons and manual notes
- Binary Switching: Extract actual code from both binaries instantly to verify similarity metrics
4. Session-Based Analysis Efficiency
- Traditional: Reload binaries multiple times, lose context between analyses
- Binary Switching: Maintain loaded binary session, switch instantly between targets
5. Comprehensive Function Profiling
- Traditional: Partial view of function from single binary
- Binary Switching: Complete function profile comparing suspicious vs. legitimate implementations
6. Dynamic Analysis Workflow
- Traditional: Static analysis approach, one binary at a time
- Binary Switching: Dynamic comparative workflow, switching based on AI guidance and BinDiff metrics
7. Quantitative Foundation with Live Validation
- Traditional: Trust BinDiff metrics without code verification
- Binary Switching: Use BinDiff metrics to guide analysis, then switch binaries to extract actual code for validation
8. AI-Guided Switching Logic
- Traditional: Manual decision on which functions to analyze
- Binary Switching: AI uses BinDiff SQLite data to prioritize functions, then switches between binaries to analyze flagged code
9. Speed and Precision with Context
- Traditional: Hours analyzing functions manually across separate sessions
- Binary Switching: SQL queries identify targets in seconds, API switching provides immediate code access from both binaries
10. Live Evidence Collection
- Traditional: Screenshots and manual code transcription
- Binary Switching: Live code extraction from both binaries with full metadata preservation
The Future of MCP-Integrated Binary Analysis
AI’s intelligent MCP tool selection represents a paradigm shift toward autonomous analysis orchestration:
- Autonomous Database-Code Correlation: AI intelligently selects BinDiff MCP tool for database queries, then chooses Binary Ninja MCP tool for code extraction based on findings
- Strategic Multi-Tool Management: AI maintains multiple MCP tool connections and selects appropriate tools for different analysis phases
- Context-Aware Tool Selection: AI determines which MCP tools to utilize based on investigation objectives and real-time analysis results
- Cross-Platform Intelligence Coordination: AI coordinates between different MCP tools to correlate threat behaviors across multiple platforms and analysis domains
- Adaptive Validation Workflows: AI strategically selects appropriate MCP tools to verify statistical findings with actual code implementations
- Intelligent Evidence Integration: AI combines quantitative and qualitative evidence by autonomously choosing optimal MCP tool combinations for each investigation phase
AI’s intelligent MCP tool selection transforms binary analysis from a manual, tool-switching process into an autonomous workflow where AI strategically chooses appropriate tools to drive code discovery and analysis decisions.
Conclusion
The integration of BinDiff’s quantitative SQLite analysis, Binary Ninja’s seamless binary switching capabilities, and AI’s autonomous MCP tool selection and orchestration has created a fundamentally new paradigm in malware analysis. Through intelligent MCP tool coordination, AI can:
- Autonomously select BinDiff MCP tools for database queries to identify functions requiring deep analysis
- Strategically choose Binary Ninja MCP tools to extract actual code implementations based on database findings
- Intelligently correlate findings by coordinating between multiple MCP tool connections
- Orchestrate complex analysis workflows through autonomous MCP tool selection without manual intervention
This represents a shift from tool-centric analysis to autonomous intelligence-driven investigation, where AI strategically selects appropriate MCP tools to guide code discovery and validate findings with actual implementations through intelligent tool coordination.
AI’s intelligent MCP tool selection doesn’t just make analysis faster—it makes it autonomous, enabling AI to automatically choose optimal tools, extract relevant evidence, and correlate findings across multiple analysis platforms through strategic tool orchestration. This creates an unprecedented level of analytical depth where every conclusion is backed by both statistical evidence from intelligent database tool selection and verified code behavior from strategic reverse engineering tool utilization.