My Friends,
Just a quick simple and very basic tutorial on how to create an automation to extract malware configuration from PE file.
I made a very simple PE file where a string will be stored at one of its PE Section. We are going to extract the string which we assume as the malware configuration file.
Here is the code
#include <iostream>
using namespace std;
int main()
{
string data = "This is the payload made by Rio Asmara and It tries to connect to http://192.1.1.10:8080. The API will connect at random time and it will try to connect to C2 server every 1 minutes with jitter 4%";
cout << "This is the configuration : " << data << endl;
return 0;
}
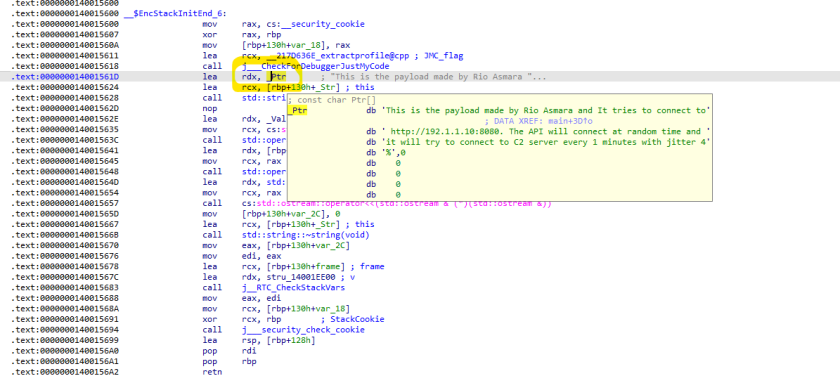
When we diassembly the above code and it will looks like this
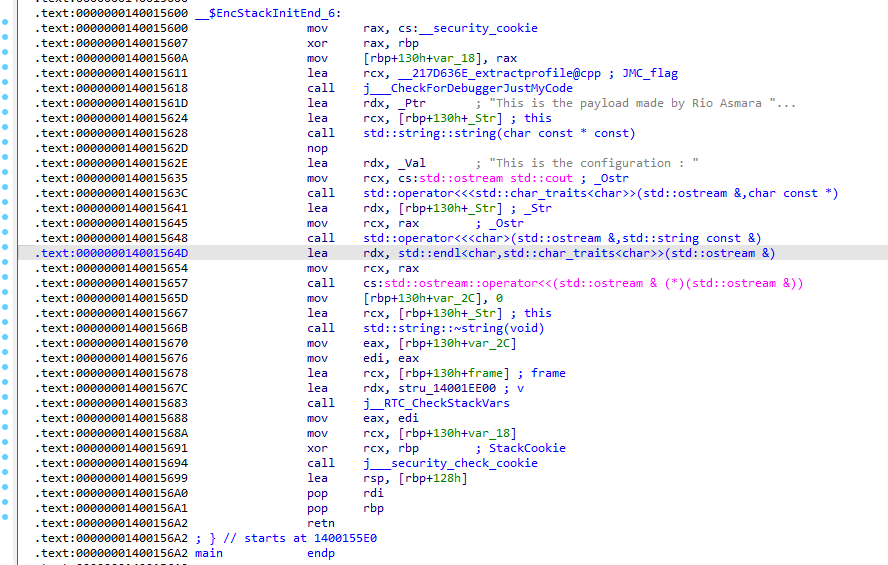
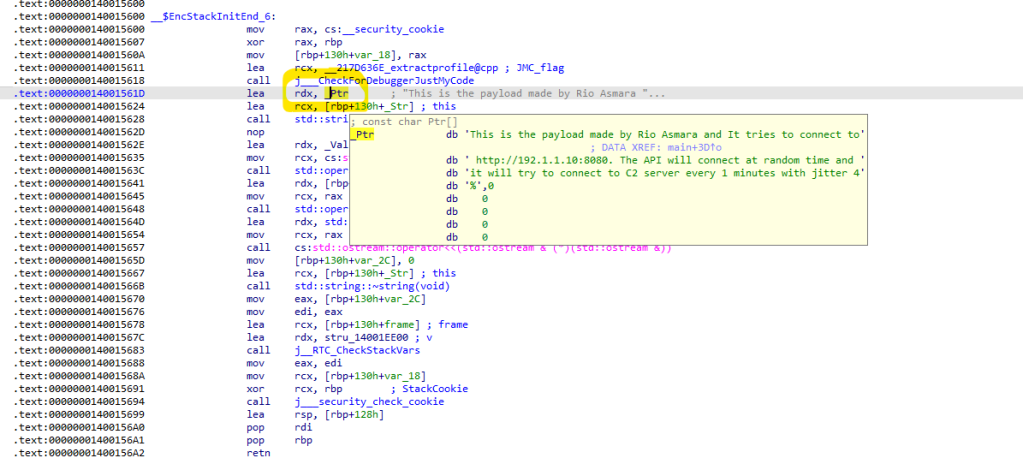
As we can do a quick look to the code, there is one string variable which we assume as the configuration of malware
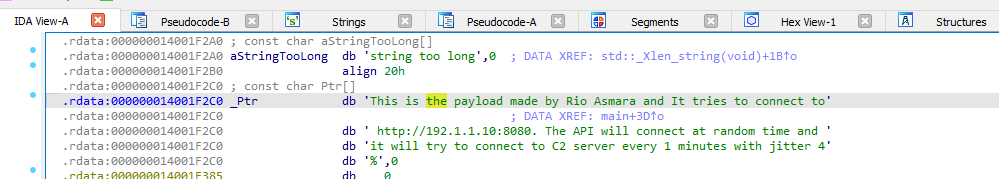
We can look at the string that it is hardcoded into the .rdata section in the PE file
I am going to create a simple python script in order to conduct the string extraction
why the scripting is really needed because extracting the malware configuration will normaly take few steps such as getting the encryption key, searching for specific string including decoding them and arrange them into something that readable by Us as the malware analyst
import pefile
def configExtract(filename):
pe = pefile.PE(filename)
for section in pe.sections:
if b'.rdata' in section.Name:
return section.get_data()
def openPEFile():
filename = input("File Name:")
data = configExtract(filename)
pos = data.find(b'This')
posEnd = data.find(b'\00', pos)
print(data[pos:posEnd])
if __name__ == '__main__':
openPEFile()
The above code is basically reads the .rdata section of the PE file. Once the .rdata section has been found and it return the data within that section.
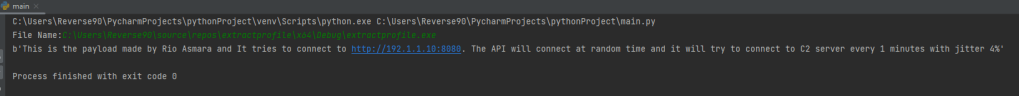
The next steps is to do the payload extraction. Since the payload that embeded is just a plain text without any encryption then it is very straight forward to do the search.
Hopefully, the above very simple code gives the idea on how to do the automation to extract the payload from the PE file