Hello Friends,
Well finally I am back after stoping for quite some times, There were many other activities took my concentration away from making a good research. 🙂
Today, I am going to write small tutorial on how to attack ADCS certificate template vulnerability. There are many tools which available on the net to make the attack more effective compared to do each step manually
What is certificate template vulnerability?
Certificate template vulnerability is caused by missed configuration which enable attacker to enroll to a certificate and impersonate any user within AD.

There are 4 items of the certificate properties that will cause a successfull attack when missed configured
- msPKI-Certificate-Name-Flag is set to 1, which means that SAN is allowed.
- mspki-certificate-application-policy contains Client Authentication (1.3.6.1.5.5.7.3.2) which means that there is a Client Authentication EKU.
- msPK-RA-Signature is set to 0 indicating that no authorized signature is required.
- mspki-enrollment-flag is set to 0 which means that managed approval is disabled.
Enumerating The Vulnerability
I have compromised an account which allow me to have access to the AD, however the access is still a low privilege user.
I will use CobaltStrike to handle my access to the compromised AD Server.
I am going to use an application called Certipy.exe which you can download from sharpcollection https://github.com/Flangvik/SharpCollection
In order to enumerate it in cobaltstrike is you need to run Certipy.exe with execute-assembly so that you dont need to upload the application to the server which make the execution less detectable
I took an example of vurnerable certificate from one of HackTheBox machine.


With the above indication, we found a vurnerable certificate which we can abuse. We can now start requesting a certificate which allow us to impersonate Administrator
Requesting a certificate
We put a request in order to generate a certificate that impersonating the administrator


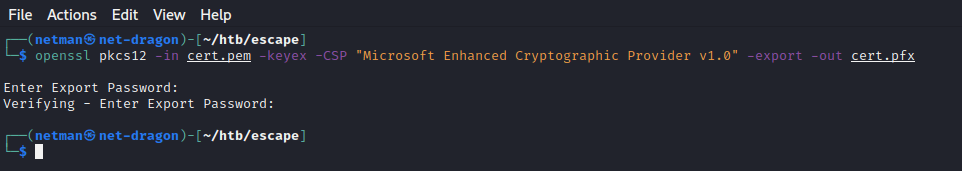
From the activities above, We receive a PEM file certificate. In order to go further then we need to convert it to pfx file
Converting to pfx file
Getting the NTLM hash of the administrator
We are going to use Rubeus in order to get the credentials of the administrator in NTLM hash.
first of all, I need to upload the pfx file to the compromised host and we will execute Rubeus with the execute-assembly from cobalstrike
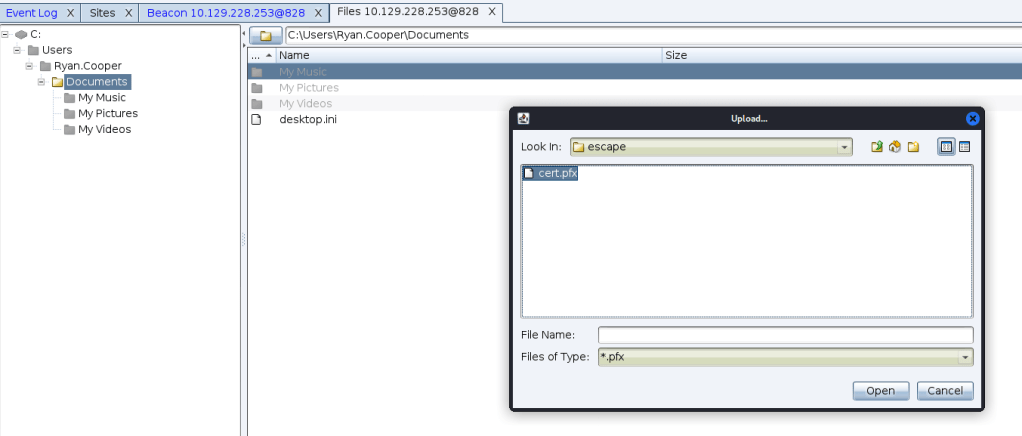
Execute Rubeus to Get the NTLM Hash
We can generate a tgt ticket by following the below command which will give the NTLM hash of the ticket.

The steps is to login with the evil winRM with the provided NTLM hash. Below is the command of the WinRM to connect using NTLM Hash.
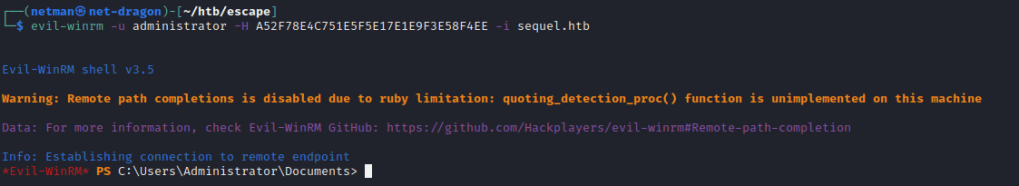
Finally we are able to escalate ourself to the local administrator of the AD server by abusing the Certificate template vulnerabilty.
The Final Step
In order to make the next lateral movement easier, I would recomment to connect the WinRM session back to cobalstrike by using beacon.

